A few years back I wrote about Personal Access Tokens (PATs) in Personal Access Tokens & VSTS. Since then, not only has Visual Studio Team Services (VSTS) been rebranded to Azure DevOps, but there is also a new PAT experience. While the original PAT experience is functional, there is a lot to be liked in the new experience.
Turn It On
At the moment, the new PAT experience is in preview. If you want to give it a try, you have to enable the option. To do this:
- Sign on to Azure DevOps
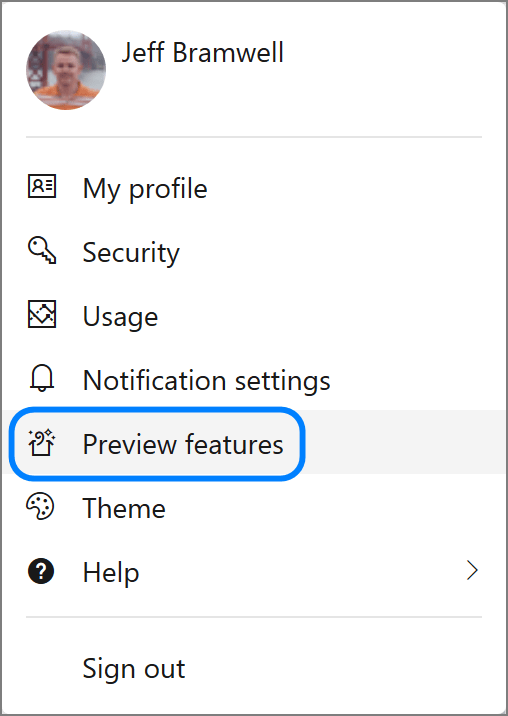
- Click on your profile image in the upper right-hand corner of the page
- Select Preview features (see Figure 1 below)
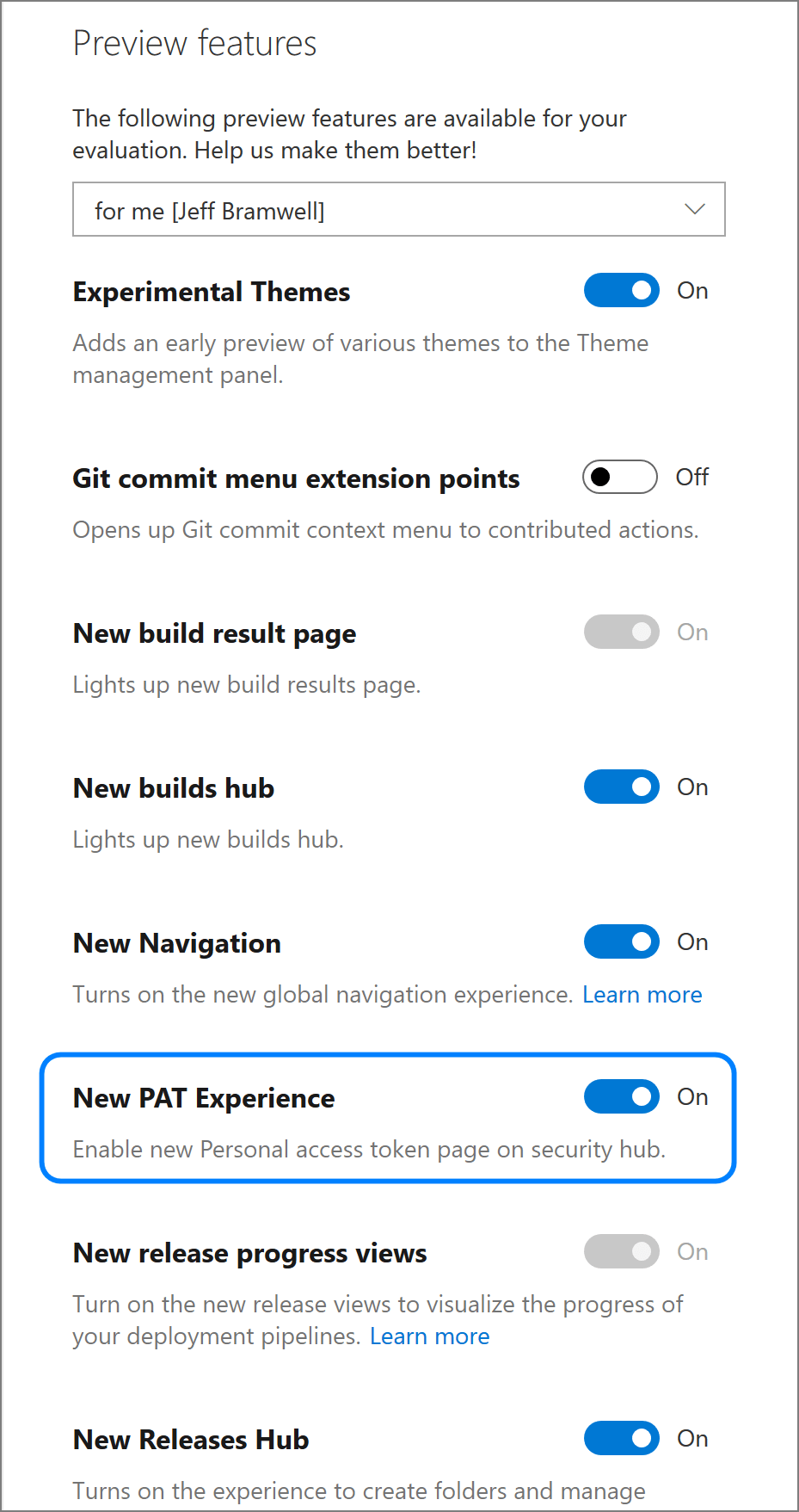
- Set the New PAT Experience option to On (See Figure 2 below) – If you don’t see “New PAT Experience” in the list of preview options, you might be reading this article after Microsoft has made this the default experience.
The New Look & Feel
With the new PAT experience enabled, click on your profile menu again and select Security (see Figure 1 above). This will display the new Personal Access Tokens screen.
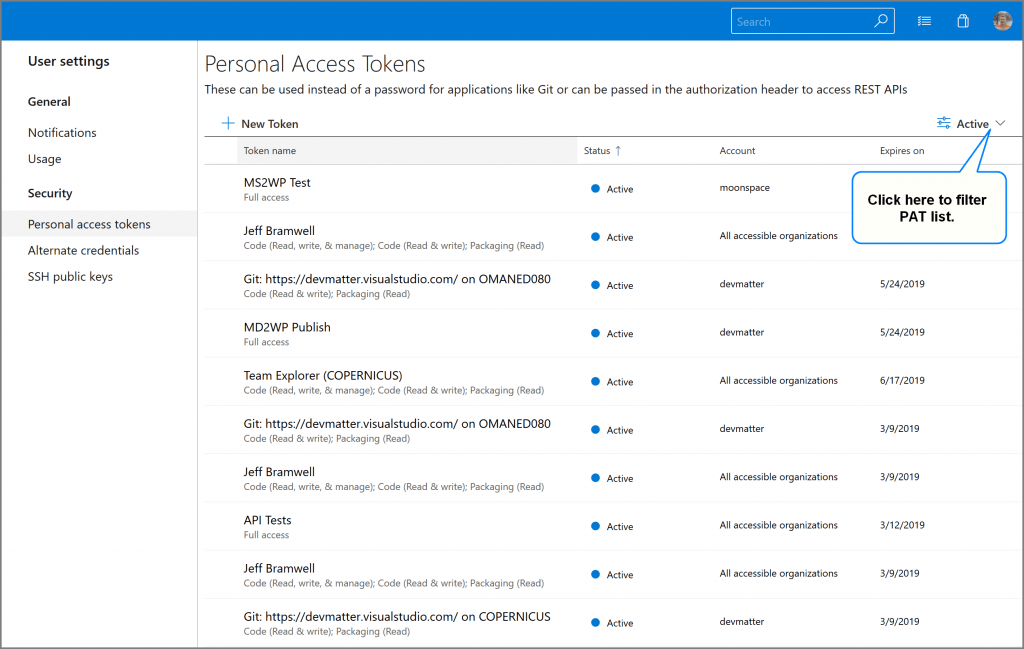
From here, you can see all of your active PATs. You can also view your revoked and expired PATs by selecting the drop-down filter on the right. Let’s take a look at a few of the features.
New Token
To create a new PAT, click on the + New Token link. This will open up a side pane where you can specify the details of the new PAT (as shown in Figure 4 below).
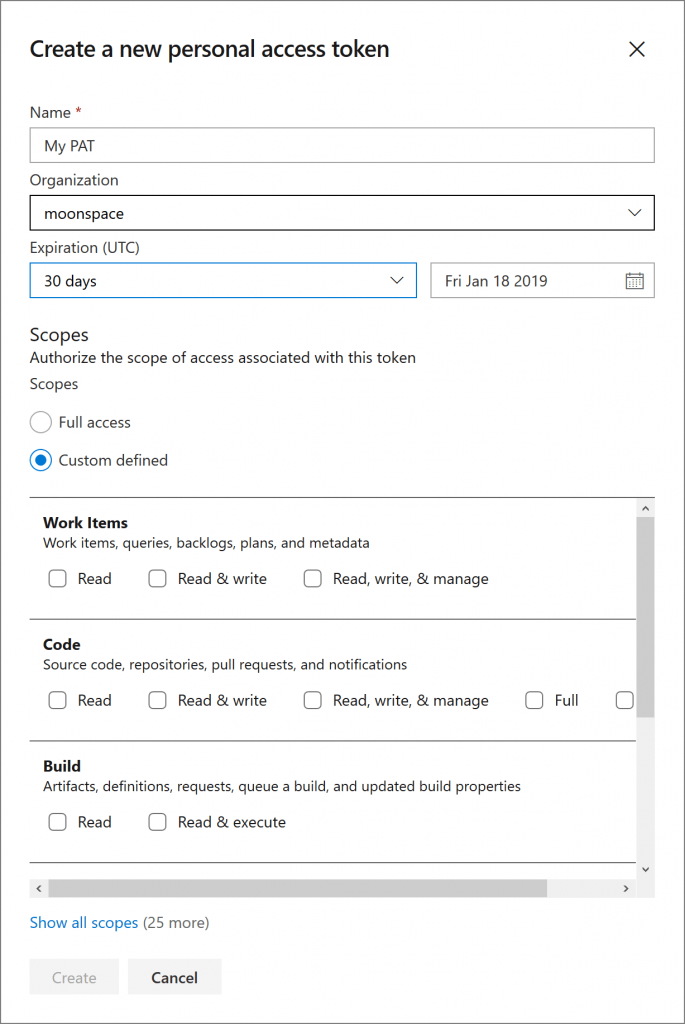
Most of what you see in the figure above is very similar to the old PAT editing experience (except it’s not a full-screen experience). One difference that stands out is that only some of the common scopes are displayed by default; You can click on Show all scopes to see them all.
Something new, however, is that you can now set custom expiration dates for your PATs as shown in Figure 5 below.
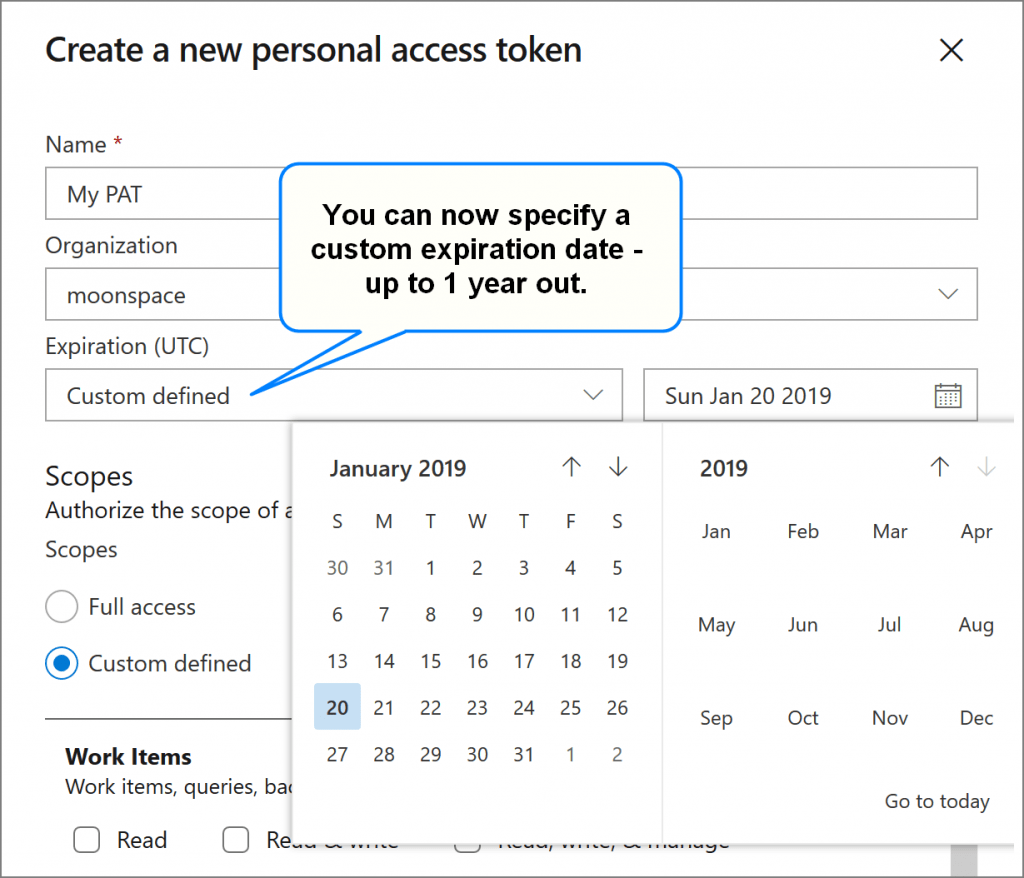
This is an extremely useful feature, for example, if you’re trying to line up expiration dates for multiple PATs for ease of management.
WISH LIST: I would really love the ability to extend a PAT’s expiration date beyond a year. Since they can be revoked at any time, having PATs with a two or three year expiration would be pretty handy.
Regenerate Token
A brand new feature in the new PAT experience is the ability to regenerate an existing token. Regenerating an existing token will keep the token’s current settings (e.g. name, organization, expiration date and scopes) but will generate a new key, replacing the old key.
To regenerate an existing PAT, select the token and click on Regenerate as shown in Figure 6 below.
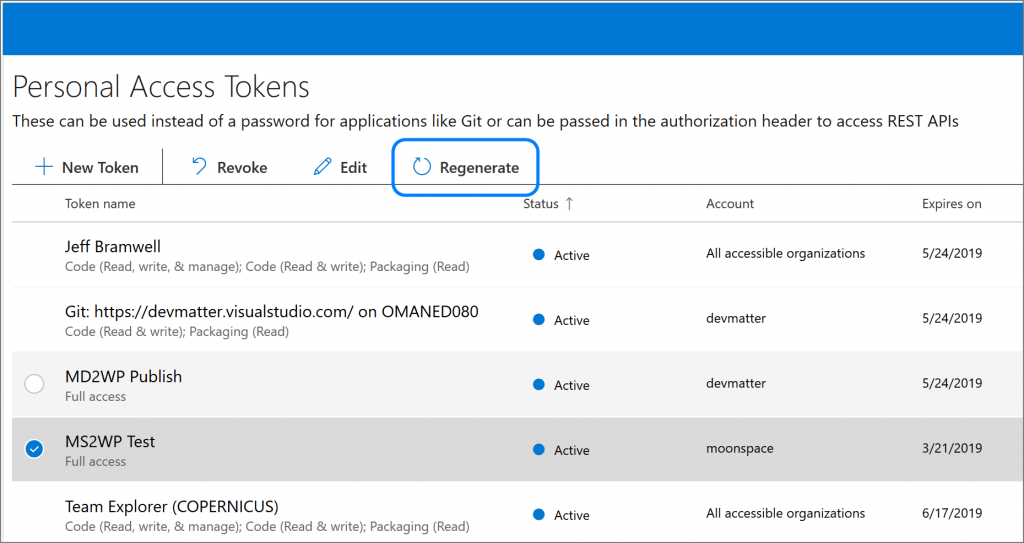
Once you click on Regenerate, a confirmation dialog will be displayed:
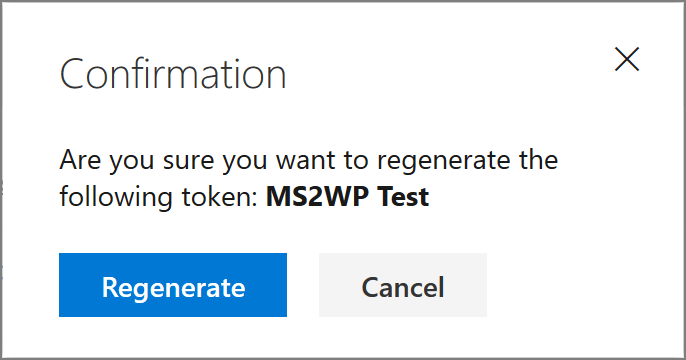
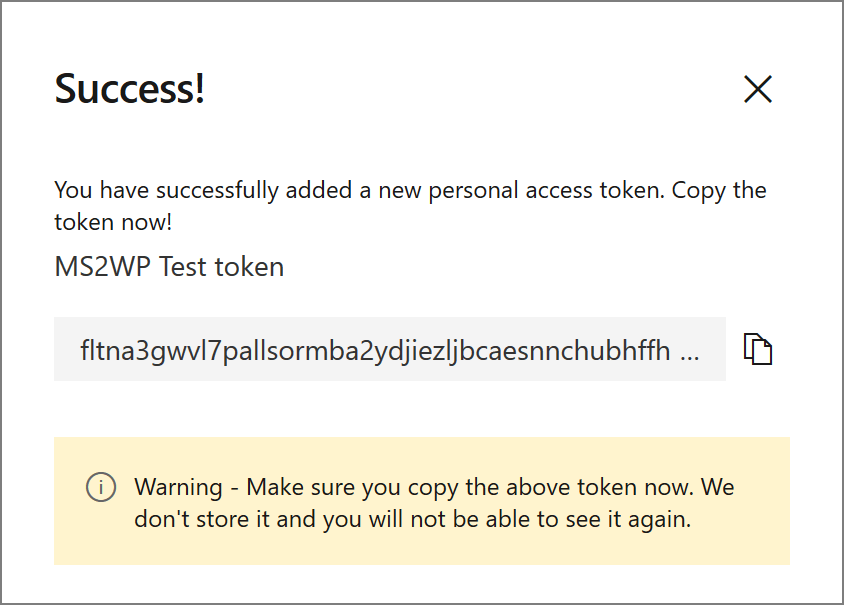
Clicking Regenerate will display a side pane displaying the newly-generated token. Make sure you copy the token and store it somewhere secure since this value can’t be displayed again once the window is closed.
Summary
All in all, the new PAT experience is a nice improvement over the previous experience. Having the ability to set custom expiration dates and regenerate existing tokens is super nice!
It’s also worth mentioning that there is now a decent set of APIs around managing personal access tokens. I will cover these APIs in a subsequent post.
If you’ve tried the new PAT experience, leave your thoughts below… do you like it better or do you prefer the older/current experience?
